The dark web, also known as dark net, deep web or invisible web, was launched nearly 20 years ago with the release of Freenet. Freenet was a decentralized network designed to be less vulnerable to attacks and snooping by authorities.
Today, the dark web is an area of the internet, which requires specific browsers and configurations to connect to it. Websites on the dark web are more secure and private. It also prevents big search engines from indexing them, which makes finding them more difficult for the everyday user.
In this blog series about the dark web, we will shed light on the dark web and share a better understanding of what the dark web is and how it’s used.
But first, to best understand the dark web, you must know the layout of the internet and some key terms.
Surface Web, Deep Web, Dark Net, and Dark Web
Internet
The internet is more extensive than most people realize. It can be divided into four distinct areas: surface web, deep web, dark net and dark web.
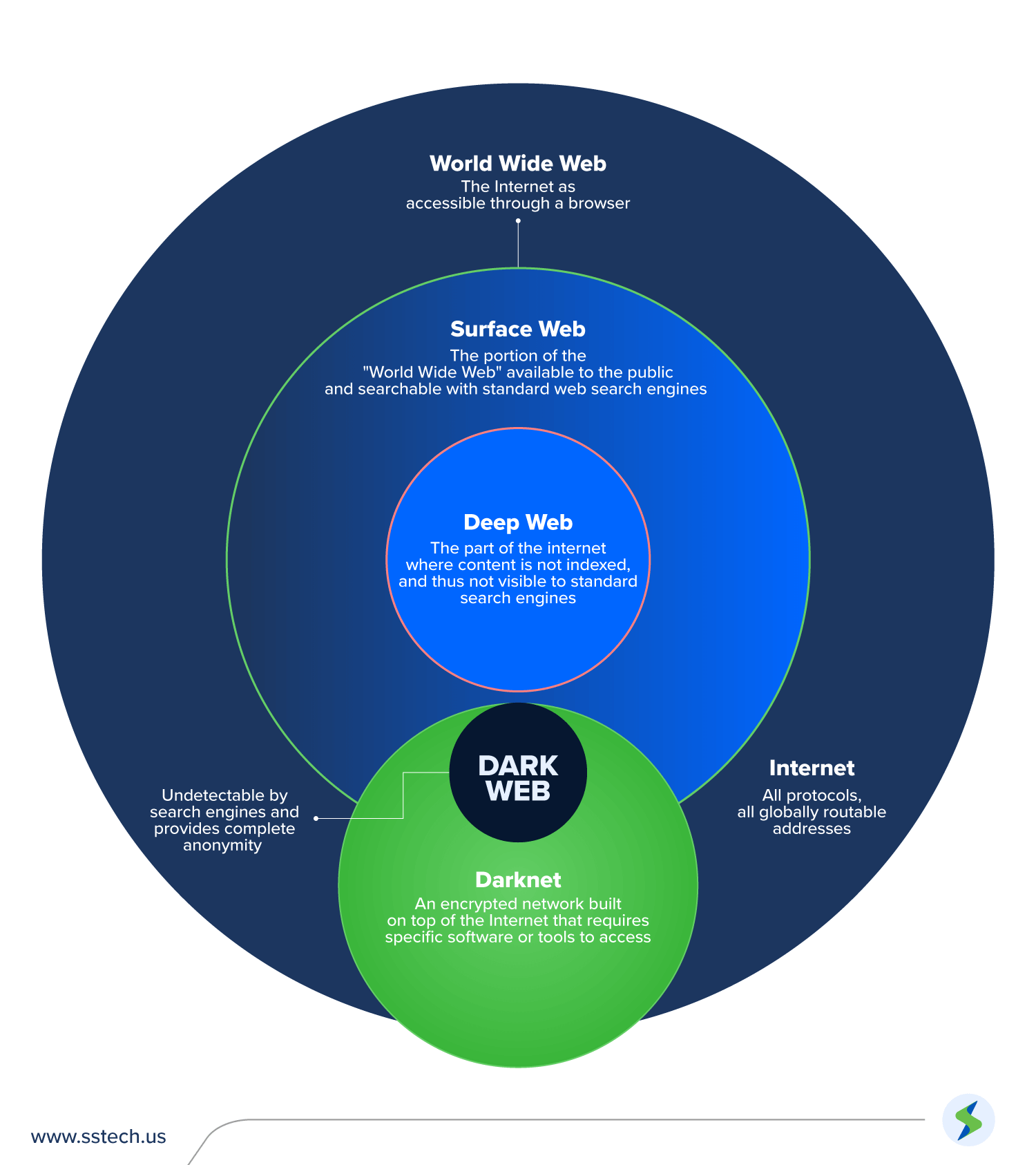
Surface Web
The surface web is everything you can see when you use a search engine like Google, Yahoo or Bing. This includes any website indexed by these search engines and made available for public viewing. The information found on the surface web includes anything from up-to-date news stories to recipes.
The key (pun intended) part of this area, from a security standpoint, is it doesn’t require encryption. A fun fact: This area is smaller than most people know. Major search engines only give you access to approximately 5% of the total content on the web.
Deep Web
The deep web or deep internet is a term referring to parts of the internet not indexed by popular search engines. It has websites hidden by password protection or paywalls.
If you have a Facebook page, for example, and it’s set to private, the only way to access it is through Facebook. That means Google can’t index the webpage. It would classify your Facebook page as a “deep web page.”
Other examples behind a paywall include Netflix content, university portals or even your bank’s website. You’re constantly on the deep web, and probably accessing it more than you think.
Dark Net
The dark net is the infrastructure and back end of the internet. It isn’t indexed by search engines and is inaccessible through a browser. But it’s still connected and facing the internet.
Despite its name and its reputation for supporting criminal networks, the dark net is used for both good and bad.
The dark net was originally developed to support people ruled by authoritarian regimes, so they could communicate with human rights activists, other governments and journalists, without fear of being censored.
On its dark side, the dark net is also for criminal activity. That includes buying and selling drugs, and trading and selling stolen personal data and other sensitive information.
Dark Web
The dark web refers to content that exists beyond the divide of hidden or concealed content.
For example, users often use the Tor browser on their computer or phone to view content they would otherwise be unable to open using a regular browser.
Other examples of special anonymity networks include I2P and Freenet.
The Tor network, aka the onion dark web, was founded by the U.S. Navy. It was later transferred to the Electronic Frontier Foundation (EFF). It’s now its own nonprofit, Tor.
Tor is the most widely used network because the more users on it the greater the anonymity for those users. They have nicely packaged access to it, so it only takes seconds to grab the browser and connect. This browser install package comes bundled with configurations already set.
However, there are others.
Firefox can be configured to set up connections to these hidden websites. Once set up, you type in a site address, then it connects you to the proper server, setting up an encrypted connection to its location. This is the same as the surface web, which is common to the average user.
On the Tor network, these extensions end in .onion, rather than .com. This naming convention originated from the ability to evade censorship and form networks to avoid government monitoring.
How Do Dark Web Markets Function?
No one can talk about the dark web without mentioning its marketplaces. They are known as dark net markets (DNMs). These services aren’t secure against law enforcement but are difficult to trace.
On DNM sites, weapons and drug dealers typically advertise and sell illegal goods and services and seek hackers for hire. It’s one of the fastest-growing submarkets on the invisible internet today. And it’s estimated at $23 billion in annual transactions, which is approximately 10 times larger than estimates in early 2015.
However, it’s not just for those trying to conduct illegal transactions. There are also those who are selling legitimate goods and services here.
Yet, DNMs are why the dark web has gotten such a bad reputation. It’s also where your personal data, if it’s been compromised, will likely be sold.
Is It Illegal to Access Dark Web?
Despite what many may think, there’s nothing illegal about the dark web. When many of us hear the term “dark web,” we imagine a shadowy underworld of the invisible internet, which we’ve been warned to avoid. That’s far from the truth.
However, this doesn’t mean there’s no illegal activities on the dark web.
The dark web’s most important feature—privacy—makes it appealing to whomever needs to cover his or her tracks for legal reasons. Or has proliferated buying and selling illegal goods and services for years.
Buyers and sellers flock to the dark web because they can trade credit card data, log-in information, forged documents, pirated videos, hacking services, drugs, weapons and stolen company data. The buying and selling of these goods and services are illegal in most countries.
There are also some content restrictions on what can be accessed via Tor’s servers. But these are no different than those imposed by other platforms like Facebook or YouTube, forbidding users, for example, from posting religious or hateful content.
Why Do People Use Dark Web?
What draws parts of the underworld to this dark cyberspace also has potential benefits for more mainstream and legal users. That feature is privacy.
According to a survey conducted by the Center for Governance Innovation and Ipsos Public Affairs, the top reason reported for using Tor to access the dark web was: “I like being anonymous online” (39% of anonymous respondents).
That was followed by 26% wanting to access unavailable content in the user’s geographic location. Privacy was next, with 25% of users reporting connecting to protect their privacy from internet companies.
The theme of anonymity came up repeatedly on the list as among the most common reasons for bypassing the surface web and going deeper.
Another reason is to avoid government censorship.
Privacy Is a Critical Commodity
Nowadays, privacy is a critical commodity. Yet, on the surface web, where you find Facebook, Twitter, eBay and an assortment of other e-commerce, social media, corporate and private websites, our privacy is constantly at risk. This is because these sites track and monetize our data for profit.
Users typically want to hide their identity from organizations that have been hacked and have been using personal information against them.
Others use it to dodge paying taxes and law enforcement. While some just prefer anonymity. There are others who live in lesser countries with far more censorship than the United States. They are looking to safely reach out, without punishment or censorship by their government.
What Will Be Found on Dark Web?
The answer to this question is complex. What’s on the dark web is the same as what’s on the world wide web: blogs, news articles, publications, DNMs (which we described earlier) and online stores and sites, which only exist on the dark web.
There are also some sites that exist in both spaces. Facebook, for example, has a dark website. This makes it difficult for authorities to trace items and find out who illegally bought them.
Some sites include illegal services, such as cybercrime forums, secret e-commerce stores for drugs and stolen information, and hacking tools to access private networks.
What’s more, according to some reports, transactions on the dark web are less susceptible to data snooping by law enforcement agencies. Many of these transactions are either illegal or involve prohibitive substances like drugs, weapons and counterfeit passports. Therefore, protection of this part of the internet’s ecosystem is crucial for both governments and criminals.
Is Dark Web Dangerous?
Browsing the dark web will not put you on any government agencies watch list. It’s considered safe—arguably safer than the surface web—because there are fewer drive-bys and virtually no java script. The anonymity keeps you safe from being tracked by service providers. And it can help protect you from sites gathering your personal data and legally selling it.
Like Facebook and Google, Tor and other programs allow users to access the network without revealing their location and identity. But using it doesn’t make you completely invisible.
As much as we hear about the dangers of the dark web, the surface web, where many of us spend a lot of time, can be quite dangerous.
So, is there value for the everyday user on the dark web? And how can you safely navigate it?
Before you plunge into the dark side, you must consider the potential dangers lurking there. Otherwise, you may find yourself in trouble with law enforcement or face threats from hackers if your guard isn’t up.
The four primary threats posed by the dark web.
1. Account Hacking and Identity Theft. The dark web has a fair share of stolen accounts. The victims are people whose identities have been hacked by cybercriminals. The hacks are carried out by will or through someone else’s negligence. Sometimes, your account is hacked when you’re simply testing a new password you have just created for verification purposes.
2. Ransomware. The dark web is not always free of malware infections. Many websites operating there weren’t written for search engines or web crawlers. Instead, they are there to add value to the site’s aesthetics and stay in front of visitors. If you happen to visit such a page on the dark web, you can fall prey to hackers.
3. DDoS Attacks. The dark web hosts online businesses with malicious intent. These malicious actors attack websites of unsuspecting victims with high frequency. They aim to take control of them for monetary gain or just showing off.
Theses DDoS attacks are carried out at the most vulnerable times. For instance, they target banks’ sites when customers are making online transactions. They attack the sites of media organizations like newspapers and TV channels, as they release their latest reports to carry out fake campaigns against political leaders or disrupt communication plans or publicly defame them.
4. Attacks by Hackers. It’s unsurprising hackers target websites on the dark web looking for vulnerabilities so they can do damage. Malware like ransomware is attributed to these attacks. Law enforcement agencies try to track down users of the dark web because of a hacker’s criminal intentions. This has led to arrests when cybercriminals are careless or in a hurry to complete a deal with their victims.
Conclusion
Today, the dark web is primarily associated with ransomware attacks and data breaches, which result in financial losses for organizations and a smudge on their brand reputation and customer confidence.
It’s where cyber criminals sell your personal data, account information, passwords and other sensitive information.
Our next blog article about the dark web will explain how organizations are considering the dark web for next-generation cyber security.
Follow System Soft Technologies on social media for updates on this and other security articles to help keep you cyber aware.
About the Author: Craig Wilson

As an Enterprise Security Architect at System Soft Technologies, Craig is a CISSP-certified tech guru with multiple IT security certifications. Craig’s roles as Director of IT Infrastructure and Security, Cybersecurity Solutions Architect and Enterprise Solutions Architect, along with his expertise on enterprise organization security and governance, authenticates him as a trusted and valuable advisor on security best practices.