Improve Identity Access Management and Security
While most security experts keep recommending organizations build a strong authentication policy and maintain hard-to-guess passwords, major Identity Access Management providers, such as Microsoft, are telling us otherwise.
It’s surprising to see best practice recommendations shift from “stronger passwords mean more security” to “no password as a means of security.”
Let’s now call this the era of passwordless authentication.
Passwords Don’t Matter Anymore
You know the shortcomings of passwords. There are too many of them and they are hard to maintain. Simple passwords are too easy to guess. Strong passwords increase the number of IT password reset requests. And there’s the likelihood users reuse them across multiple systems or insecurely store them.
The time it takes a modern computer to crack a password, based on its length and complexity and assuming the hacker knows basic password requirements for the application, ranges from instantaneously to more years than you can count and comprehend.
Passwords have become one of the primary sources of frustration for users and IT teams. The only ones who still love them are hackers. A 2019 Verizon breach report shows 81% of data breaches involve weak, default or stolen passwords.
Consequently, passwords have been a top target for attacks. And this has increased with the rise in remote work, thanks to the coronavirus pandemic. Hackers rely on users not following security best practices when working from home in what seems to be a secure environment.
During last year’s SolarWinds breach, a weak default password — “solarwinds123” — was one of the biggest vulnerabilities hackers exploited. It ended up being one of the most damaging hacks in history.
Securing your organization’s systems and data, using a traditional password method, is no longer practical for a mature security posture.
Implement Passwordless Authentication
With remote work and now using your own device the new reality, it’s time for your organization to securely onboard users and provide better passwordless authentication. The current shift has destroyed the traditional concept of only securing corporate premises and networks.
Now, you must protect identities, as they can be anywhere.
In most modern systems, credentials are managed and owned by a third-party Identity Provider (IDP) or broker. Your organization needs a solution that gives you back ownership and control of all credentials.
Recent surveys show more than 90% of IT professionals believe delivering a passwordless authentication for end users is the future for their organization.
A future without passwords is now a reality. And there’s available technology to support a passwordless environment. Most organizatons have already begun this journey. They have implemented passwordless authentication solutions, such as Multifactor Authentication (MFA) or Single Sign-On (SSO), which are first steps in embracing this new era.
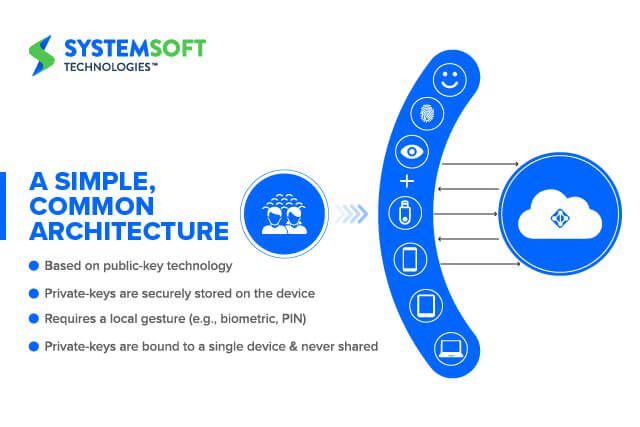
How Does Passwordless Authentication Work?
The prime question when implementing passwordless authentication is: “Will the solution ever be enough to secure my company data?”
While password authentications are inconvenient and less secure, MFA authentications are useful. But they also come with their own set of challenges, such as “man-in-the-middle” and phishing attacks. True passwordless solutions must combine both convenience and security.
If you’re implementing true passwordless authentication, you must look at decentralized authentication.
Decentralization entirely eliminates passwords. It enables communication with users through Public Key Infrastructure (PKI). PKI is a set of roles, hardware, software, policies and procedures needed to create, manage, distribute, use, store and revoke digital certificates and public-key encryption.
PKIs create digital signatures as unique credentials for people and devices, so they can be accurately authenticated at scale.
Once encrypted PKI is in place, a public-private key pairing must be devised. Private keys are only stored in the end user devices (Windows Hello, Fido2, et al). The public key is registered with the service provider, such as Microsoft Azure Active Directory.
During the authentication, the system communicates with the service provider through a token. This happens instead of applying a user’s biometric template or personal identification number (PIN).
Credentials don’t leave the local devices. And they are never shared. Your users will have everything they need on their devices to be authenticated. There’s no intermediary, putting them in control of their credentials. This also eliminates the mass credential store on the business end.
Why Passwordless Authentication?
We now understand the traditional use and storage of passwords is not enough to keep your applications, business data and personal information secure. It’s time for both organizations and consumers to rethink ways they authenticate users.
MFA and SSO are both a good start.
However, a true and mature passwordless experience will provide a smarter, more context-aware authentication.
With Zero Login/Continuous Authentication, your unique environment can become more secure. Then, all you need to do is perform a gesture or tap a wearable device, logging in to all your applications for the entire day.
One last item. Throughout your passwordless journey, you will realize passwordless and Zero Trust can’t be separated. Zero Trust is a concept that asserts no entity can be trusted — internal or external. Anyone or anything must be verified before being granted access to your resources.
Passwordless authentication eliminates the worry of who enters the credentials. By doing so, it helps increase Zero Trust levels.
Conclusion
System Soft Technologies can partner with your organization as a trusted security advisor to help you start your passwordless journey.
Typically, such a journey begins by putting in place solutions like MFA and SSO to reduce daily password use. Then, technical solutions are implemented like WebAuthn, FIDO2 and Windows Hello. This leads to the elimination of static passwords in your legacy applications.
Our team of password security experts will partner with you, as you achieve your Zero Login/Continuous Authentication maturity level.
Contact System Soft to learn more about protecting your organization.
P.S. Our next blog article about password security will elaborate on the passwordless maturity scale, the different authentication methods and available solutions. And everything else you will need to continue your passwordless journey.
Follow System Soft on social media to stay up to date on the next published security blog article.
About the Author: Ali Hamici

As an Enterprise and Cloud Security Architect at System Soft Technologies and with more than 20 years of IT security experience, Ali can gain a thorough understanding of any organization’s system and then deliver Cloud Security through Posture and Maturity Assessments, Architecture Reviews, Audits and Compliance, Governance and Risk Analysis. He provides guidance and solutions to close security gaps, promote security posture and create strategic roadmaps, which improve systems security through both hardware and software.